Single Sign-On (SSO)¶
This feature is available for accounts with the Pro plan.
Standard OAuth Login (git providers)¶
The standard authentication mechanism that CodeScene.io uses is based on the OAuth2.0 integration with Git providers such as GitHub, Bitbucket, GitLab, and Azure DevOps. This is the normal mode of operation but it has two downsides:
You must have a git account in the organization - e.g., you must be a member of your company’s GitHub organization. - Some people, such as managers, might not have such an account
Manual user management - Every user must be manually invited to the CodeScene account and accept the invitation by using the invitation link
Enterprise SSO (Microsoft Entra)¶
To address the challenges, we implemented SSO based on OpenID Connect (OIDC) protocol. At the moment, we only support Microsoft Entra .
Here’s an example SSO configuration :
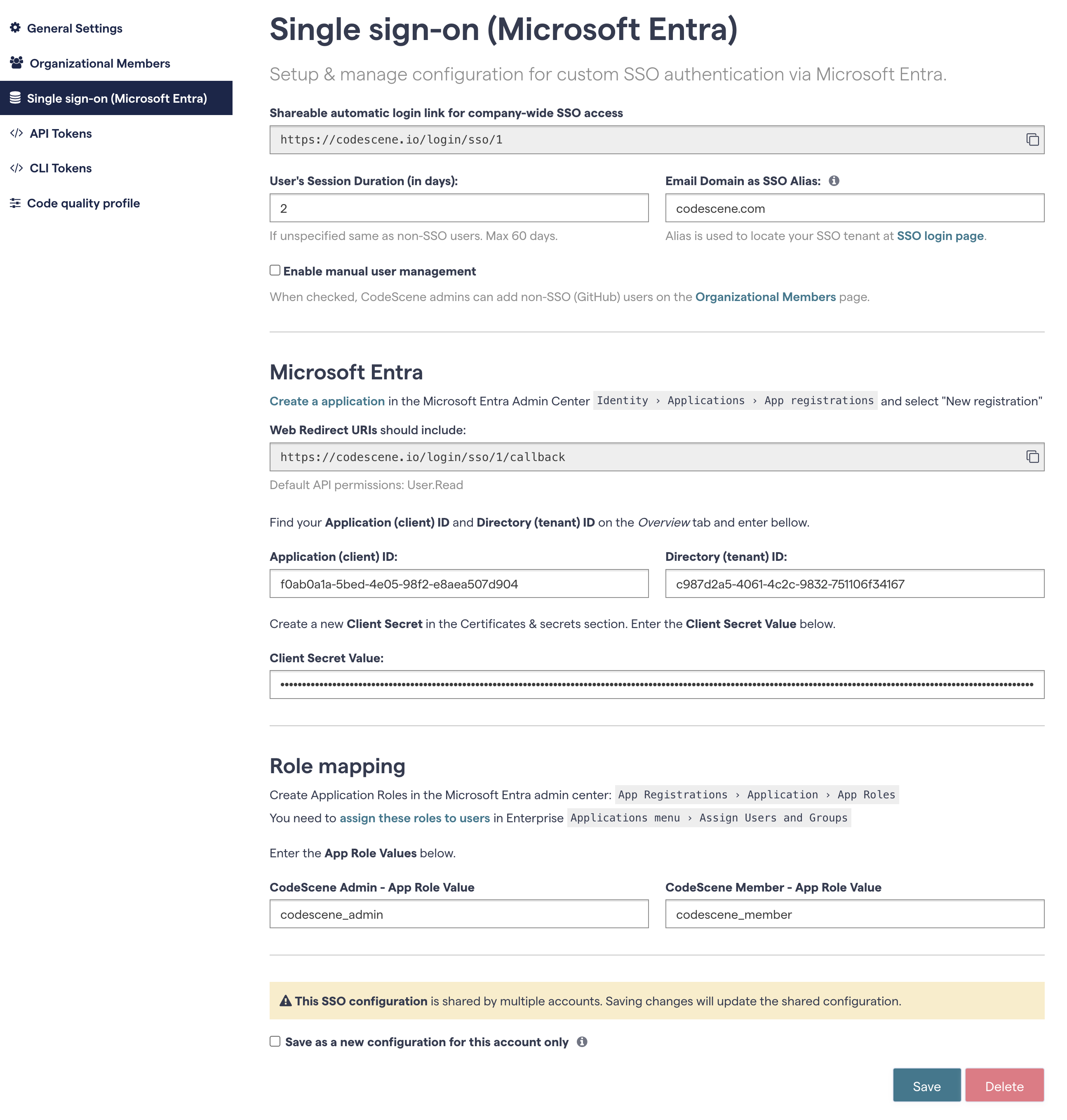
Fig. 218 Complete SSO configuration.¶
The configuration is explained in detail in the following sections.
SSO Setup¶
Microsoft Entra setup¶
The first step is to create a new Microsoft Entra application in the Microsoft Entra Admin center .
Choose Applications › App registrations > New registration.
Fill in the name and Redirect URI:
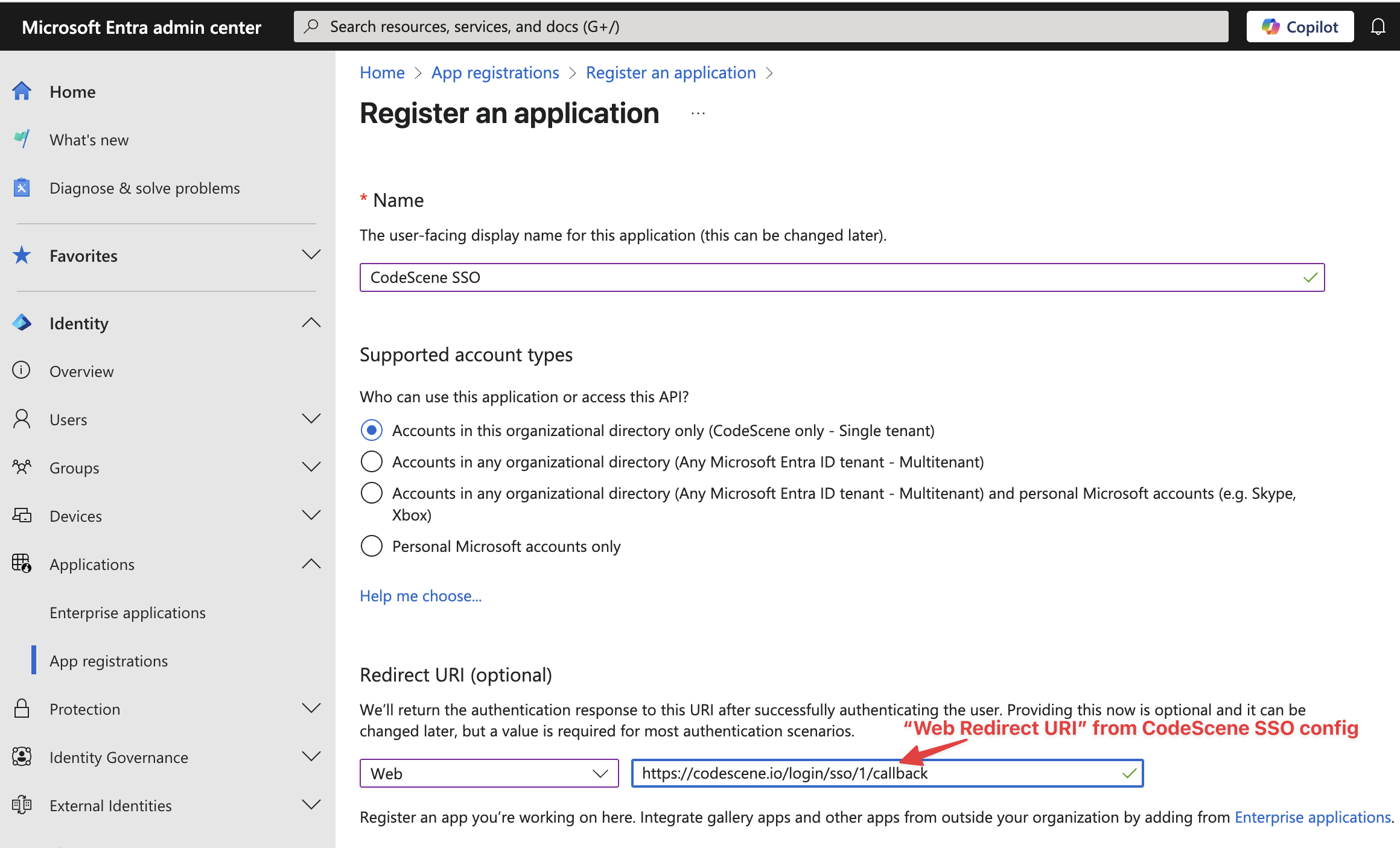
Fig. 219 New Entra app registration¶
The Redirect URI will be displayed in the CodeScene SSO config after you save the configuration (you can save an empty configuration too). Alternatively, you can skip the redirect URI specification and add it later via the “Add a Redirect URI” link in the Entra App overview page.
Proceed by copy-pasting client ID and Directory ID into CodeScene SSO configuration. You will also need to create a new client secret - follow the “Add a certificate or secret” link or choose the “Certificates & secrets” menu on the left side. We recommend using the maximum expiry time of 2 years (see Microsoft Entra app config section below).
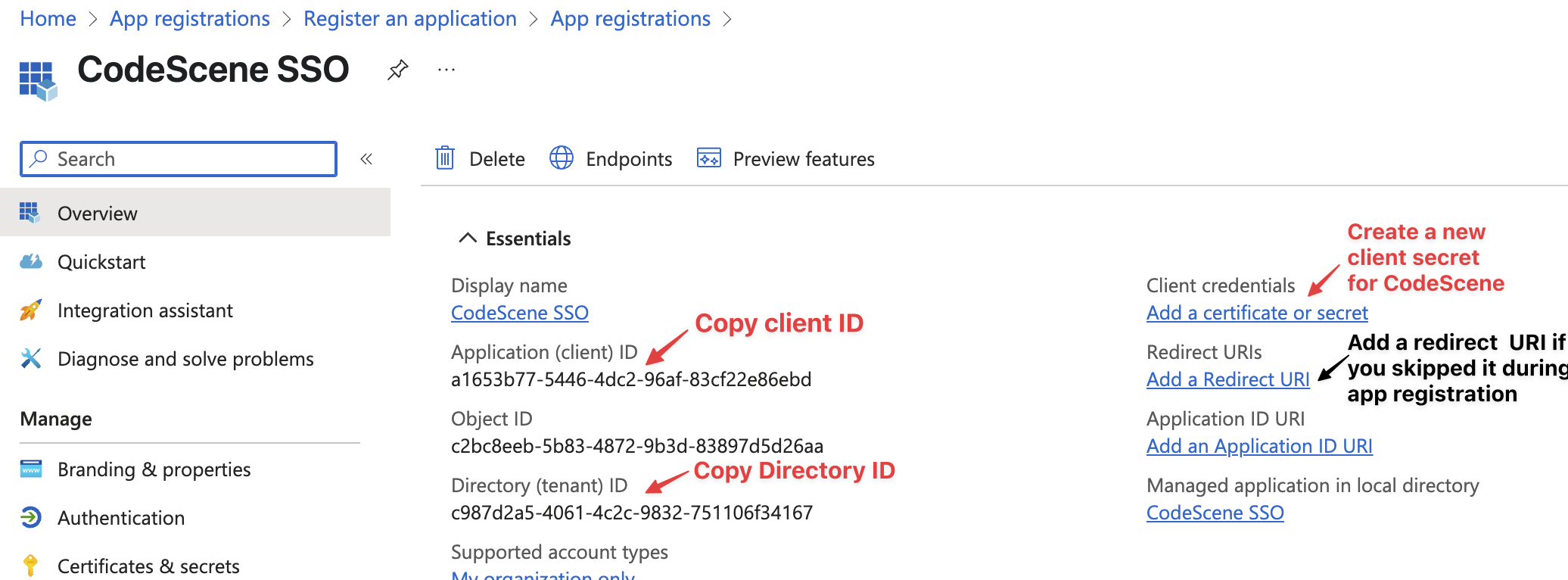
Fig. 220 Entra application configuration¶
CodeScene SSO config¶
NOTE: To setup SSO, you need to be an admin or an owner of your CodeScene org account. The owner can never be an SSO user and must log in with their Git account.
The SSO configuration page is split into 3 parts:
Generic SSO config at the top - login URL, session duration, etc.
Microsoft Entra - the client configuration
Role mapping - mapping between Entra App roles and CodeScene user roles
Generic SSO config¶
This is where your SSO login link is displayed. The login link has the form /login/sso/<tenant_id>, where tenant_id is a unique number assigned to your CodeScene SSO tenant. Your users can bookmark this link for seamless automatic login to the application. If they aren’t already logged in to their SSO provider account they will be asked to complete the authentication step. Otherwise, they will be automatically redirected to the home page (Projects dashboard).
User’s Session Duration can be used to customize the default CodeScene session duration (10 days). We recommend keeping this value short (1-2 days) because it affects how fast the changes in Microsoft Entra (a user is removed from Entra or their Entra App roles change) propagate to CodeScene. In the worst case, you need to wait a full “session duration” cycle before a removed Entra user loses their access to your CodeScene account.
In the future, we plan to implement an automatic synchronization between Entra and CodeScene, so that users will be off-boarded / updated immediately.
Users that are removed from Entra, will typically never try to log in to your CodeScene tenant again. However, they will still show up on the “Organization Members” page (see below). If this is a concern, you can remove them manually using the “Delete” button.
SSO Alias allows you to configure a memorable alias for your tenant ID. The alias is typically your company (email) domain. Your users can enter this alias on the /login/sso page. This is important for a good login experience of first-time users or existing users with a new device and/or cleared cookies. See SSO login page (/login/sso) below.
Finally, Enable manual user management controls the “Add Member” button on the Organizational Members page. By default, the button is disabled when SSO is activated for a CodeScene account. This encourages administrators to manage all their CodeScene users on the SSO provider’s side. However, if you have a mix of SSO and non-SSO (git provider) users in your account, you can check Enable manual user management and then add git users manually via the “Add Member” button.
Microsoft Entra app config¶
We have already described how to create a Microsoft Entra application above.
Let’s recap the CodeScene configuration fields:
Application (client) ID - the ID of the specific application you have created for CodeScene SSO
Directory (tenant) ID - the ID of your Entra tenant/organization
Client Secret Value - the secret you have generated in the “Certificates & secrets” section of your Entra app config
Make sure you copied all the values from the Entra app configuration and pasted them into proper fields.
NOTE: Entra app secrets have limited validity. When they expire, your user’s experience might be disrupted and you have to promptly replace them with new credentials. To minimize these interruptions, we recommend the maximum expiry time (2 years) when creating the CodeScene app client secret.
Role mapping¶
After enabling SSO, no Entra users get automatic access to your CodeScene account. Instead, they must be granted specific “app roles”.
For that, you must first create these roles in App Registrations › <Application> › App Roles. You will want one role for admins and another role for members in your CodeScene account(s):
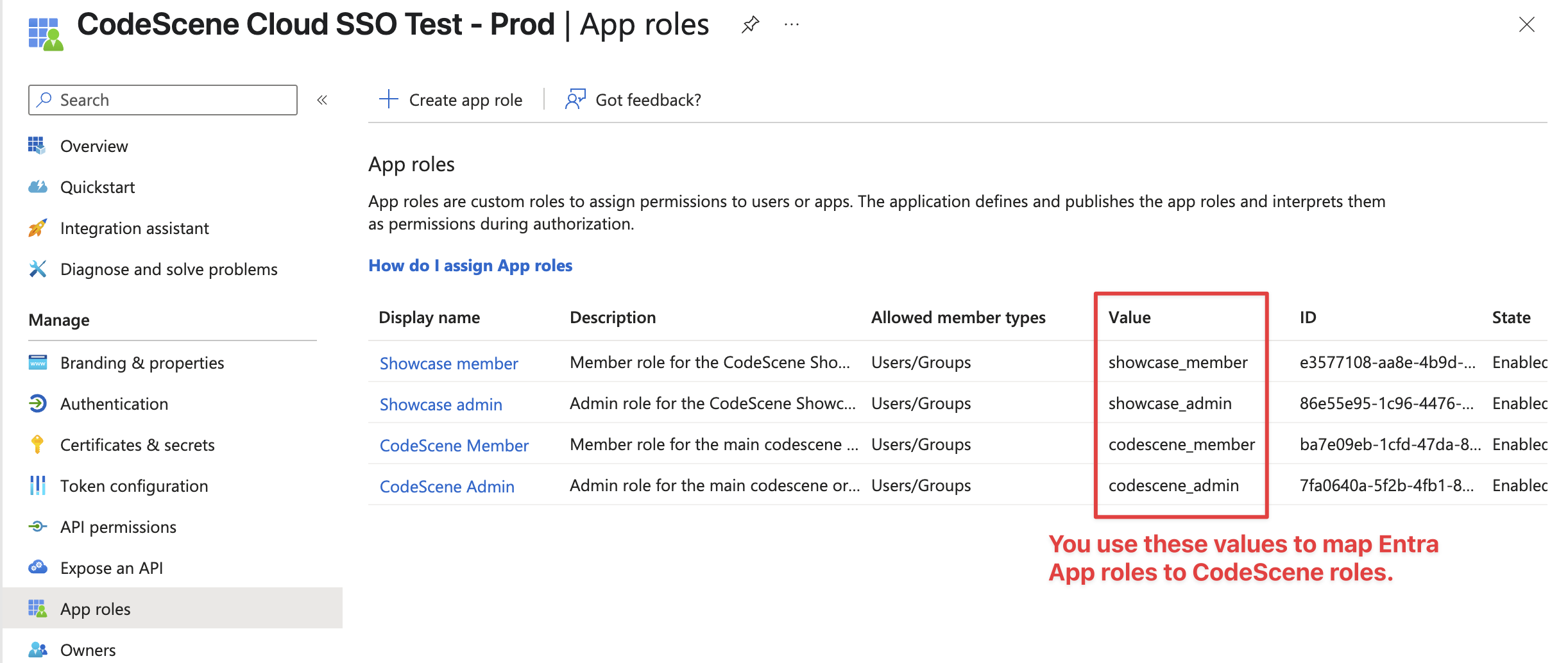
Fig. 221 Entra App Roles - two different accounts sharing the sso config (two roles for each account)¶
Above, we can see four roles in total because this SSO configuration (Entra Application) is shared by two different CodeScene accounts, named ‘Showcase’ and ‘Codescene’.
Then you need to assign these roles to users in Enterprise Applications menu › Assign Users and Groups:
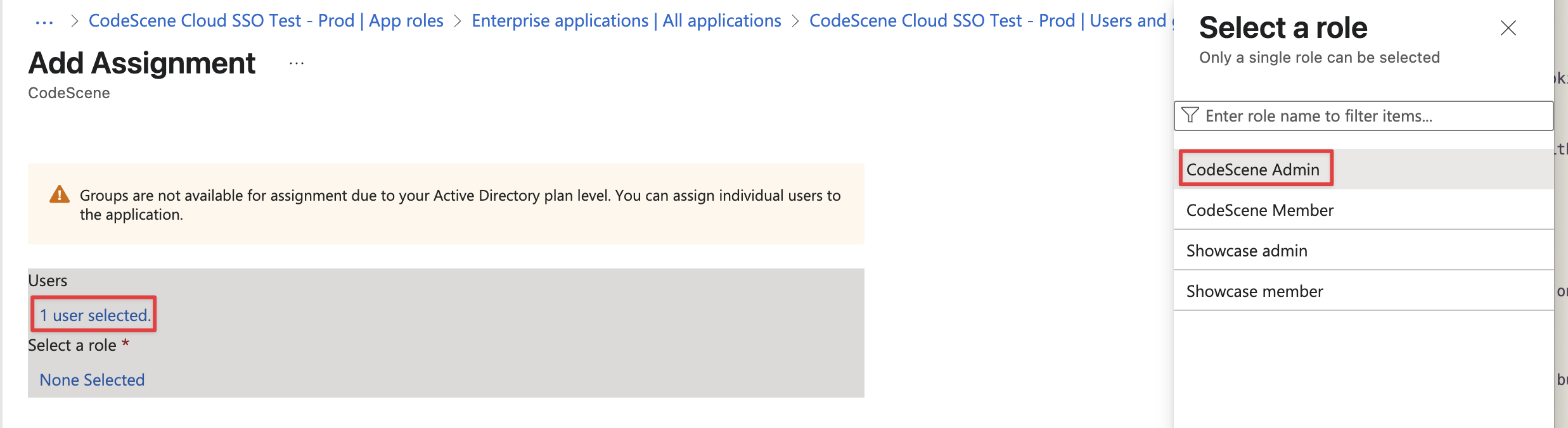
Fig. 222 Entra App Roles assignment¶
Multiple CodeScene accounts sharing the same SSO config¶
Some organizations have multiple CodeScene org accounts because they have multiple different Git (e.g. GitHub) organizations. In that case, you most likely want to create a single Entra application and share the SSO configuration between all your CodeScene accounts.
This is achieved by entering the same configuration on the SSO configuration page and using the same alias for all your accounts. You need to do this for each account separately by switching to it on the My Accounts page and then filling in the SSO config (again).
Make sure all the configuration values are the same except the Role mapping (the roles can be different for each account). Here’s an example of two different accounts sharing the same SSO configuration, but using different roles (see also the Entra App roles shown in the previous section):

Fig. 223 CodeScene SSO config - role mapping - ‘CodeScene’ account¶

Fig. 224 CodeScene SSO config - role mapping - ‘Showcase’ account¶
SSO login page (/login/sso)¶
After you configure SSO for your CodeScene account, Entra users with proper App roles can log in using the /login/sso page.
First-time users will need to enter your SSO tenant alias (typically a domain name) or ID:
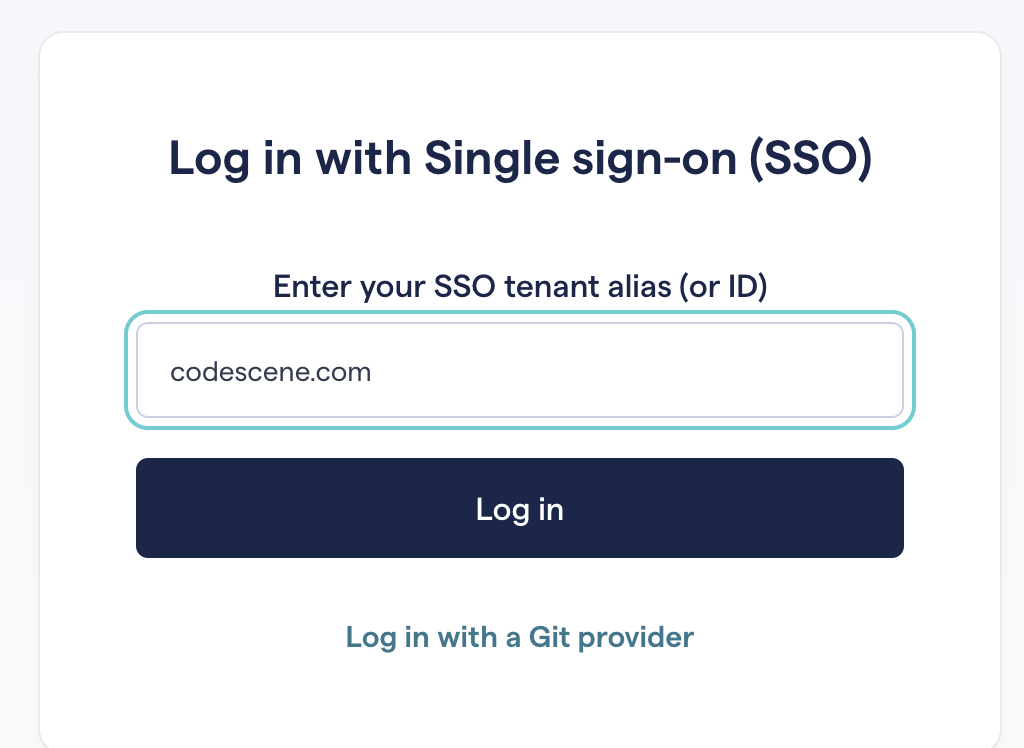
Fig. 225 SSO login page.¶
Alias is less important for returning users because their tenant ID will be stored in a browser cookie and they can use the quick login button:
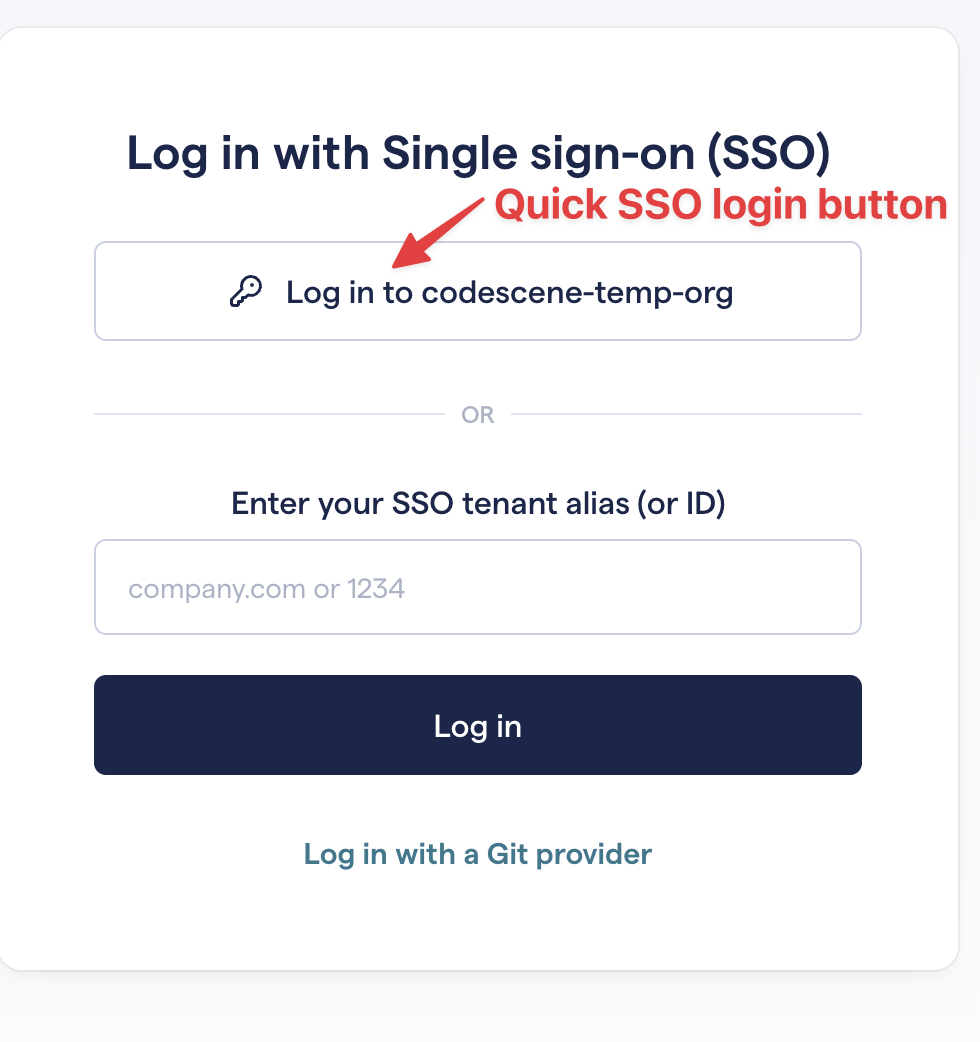
Fig. 226 SSO login page - quick login button¶
A similar button will be displayed on the main login page (/login) too.
After we release the feature to the general public, there will also be a link to the SSO login page on the main login page.
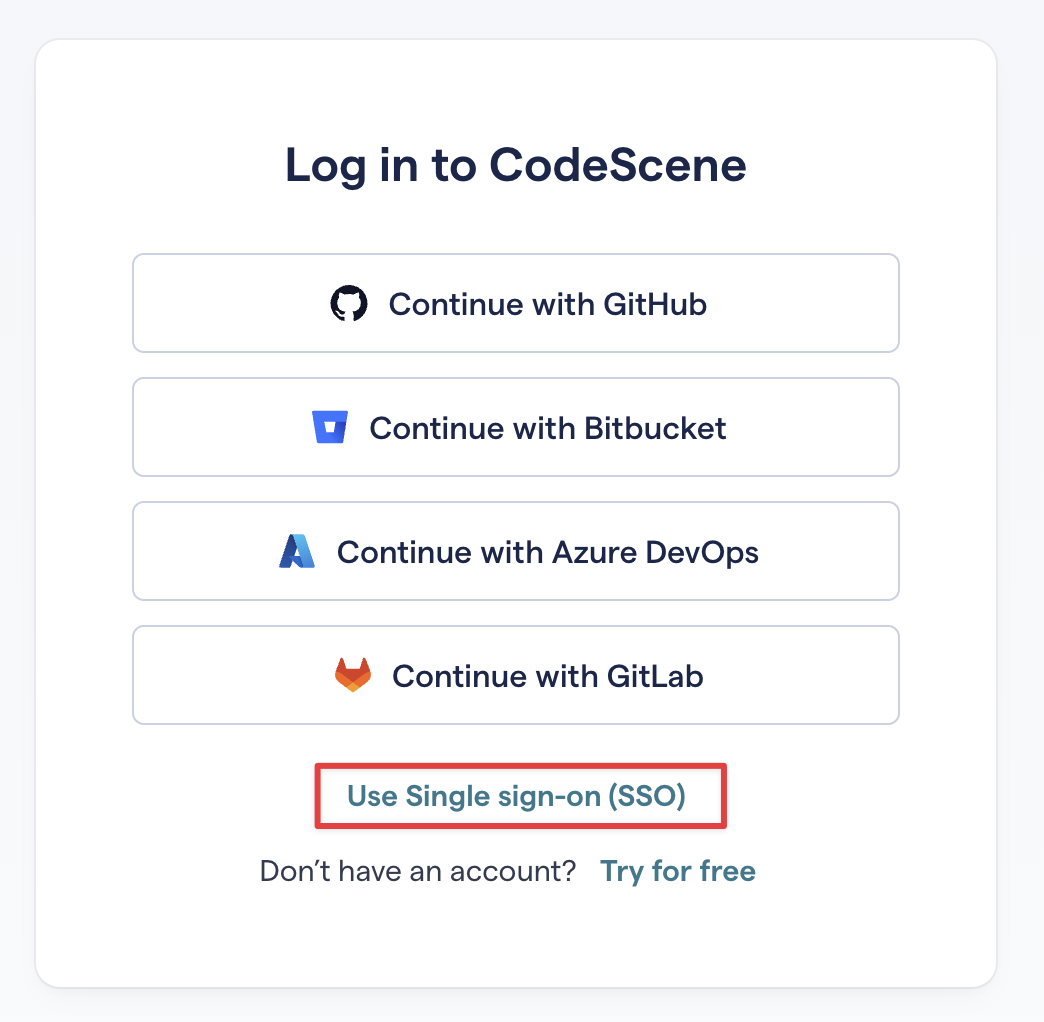
Fig. 227 Main login page with SSO link¶
Organization members¶
With SSO, most user management is automatic so you might not need to use the Organizational Members page at all.
However, it can be useful if you can get a quick overview of your actual CodeScene users, have a mixture of non-SSO (git) and SSO users, or need to remove users manually.
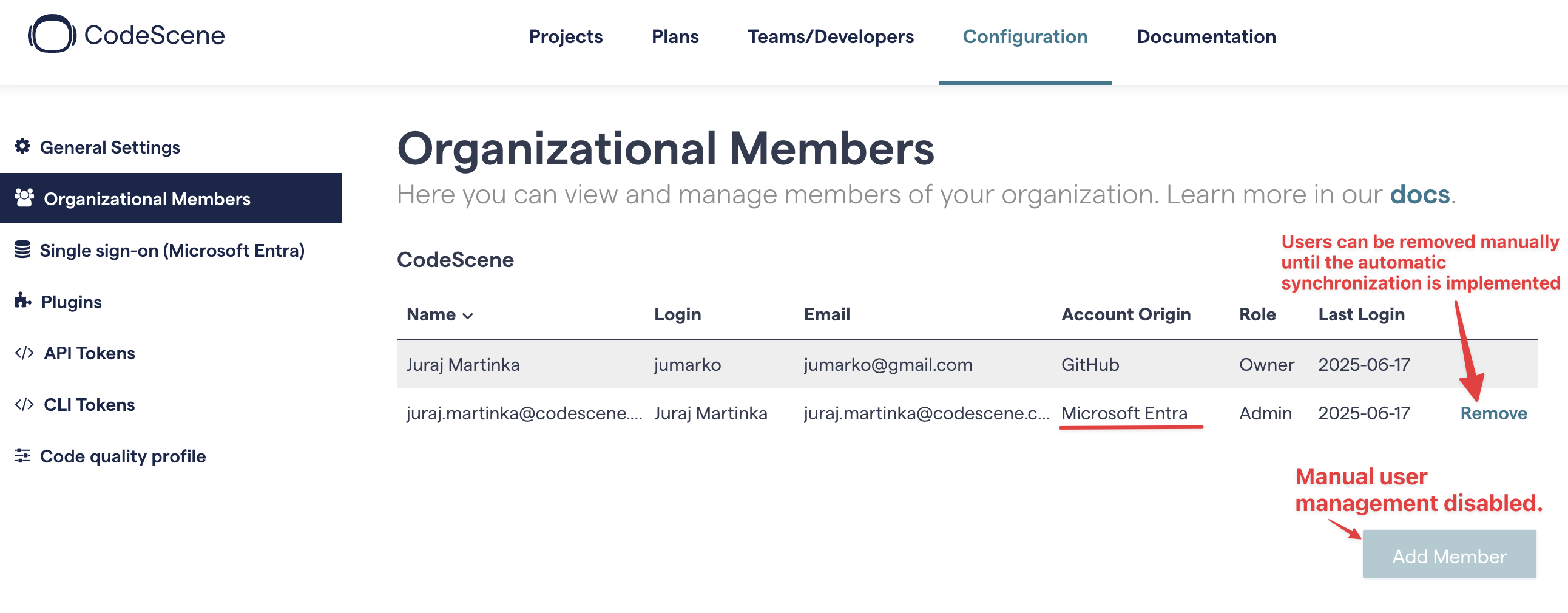
Fig. 228 Organizational Members page - showing one SSO user¶